Overview

Overview
zkTLS (also known as "web proofs" or "MPC-TLS") is a cryptographic technology that verifies the authenticity of TLS data while preserving privacy, all without requiring modifications to the data source servers. This innovation enables the secure utilization of personal data stored in siloed Web2 servers, facilitating seamless and cost-effective cross-platform data flow.
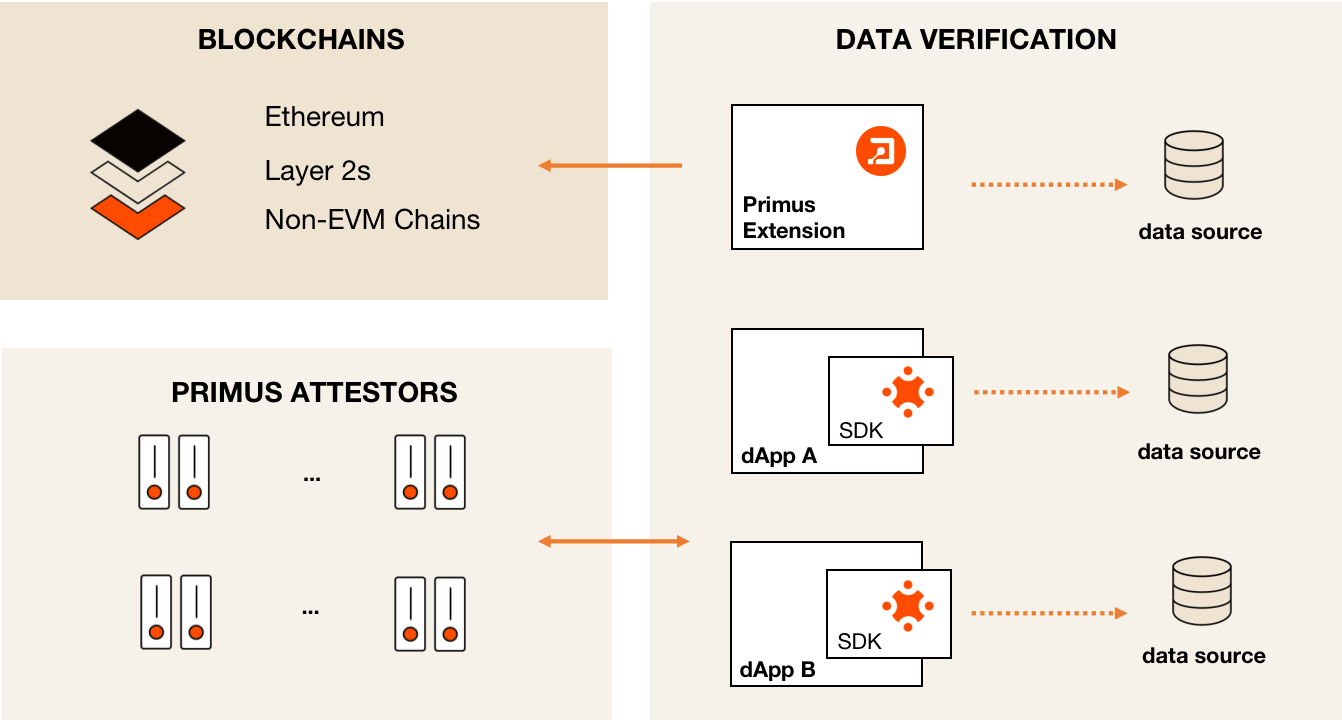
In the industry, two primary modes are commonly used for zkTLS: the MPC mode and the Proxy mode. Each mode presents its own trade-offs in terms of security and performance. Primus addresses these differences by providing unified APIs, allowing developers to choose the most suitable mode based on the specific requirements of their applications.
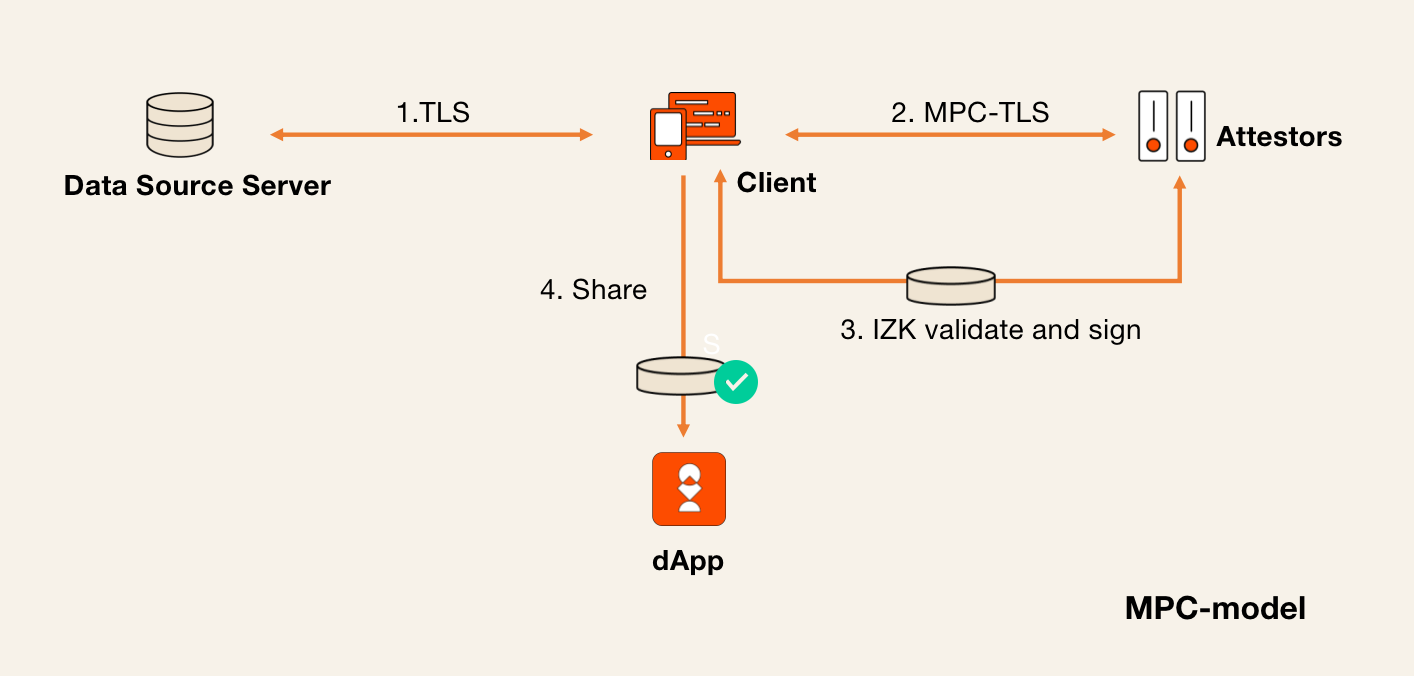
MPC Mode
In the MPC mode, the attestor and the client collaboratively execute a secure multi-party computation protocol to generate the materials needed to set up a TLS session with the data source server. This ensures that the client cannot control or modify the TLS data before the attestor sends back its share of the session key.
The key advantage of Primus' MPC mode is its use of the highly efficient and lightweight interactive zero-knowledge proof system, QuickSilver, developed by the Primus team. QuickSilver significantly reduces both computational and communication overhead, enhancing performance. For more details, please refer to our technical whitepaper.
The diagram below illustrates the general workflow of how the MPC mode operates.
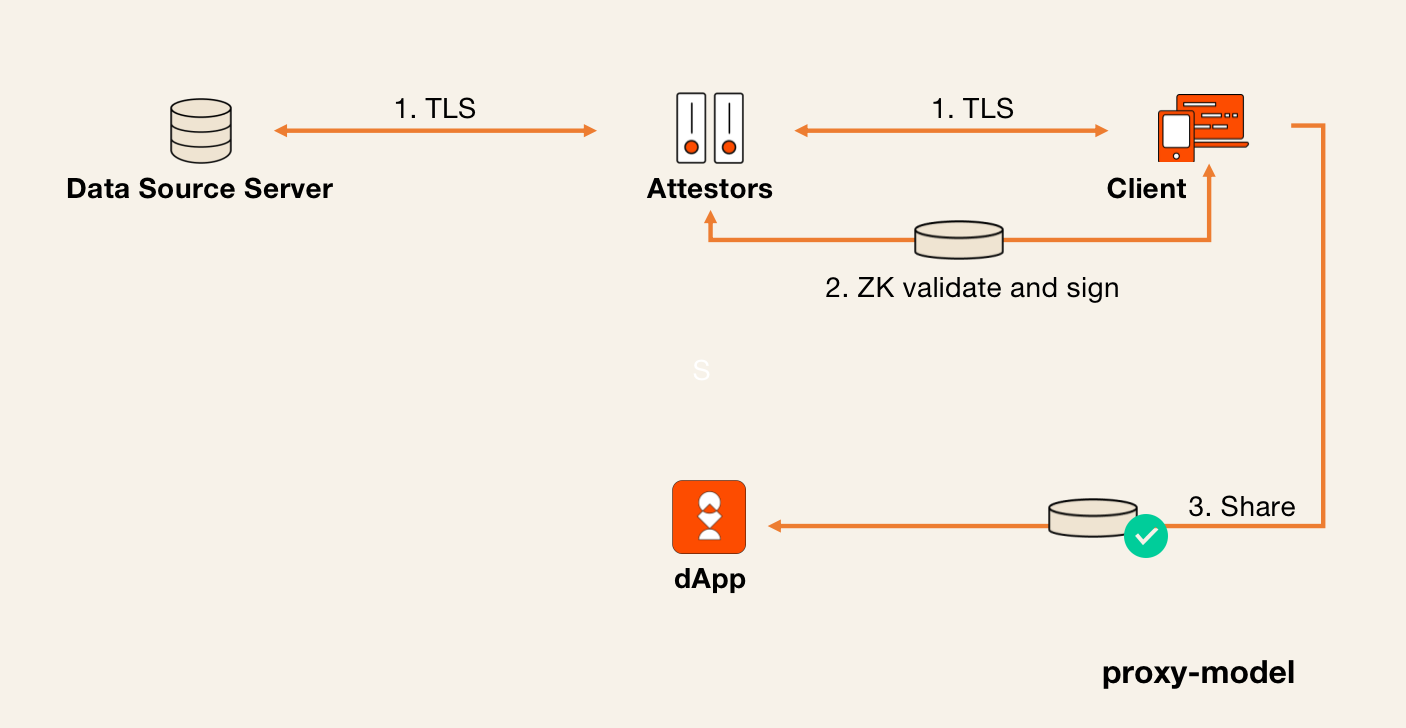
Proxy Mode
In the Proxy mode, the attestor acts as an intermediary between the client and the data source server, forwarding TLS traffic between them. Additionally, the attestor records all ciphertexts exchanged between the client and the server. At the end of the session, the client must prove to the attestor that it knows the plaintext messages underlying the ciphertexts.
The Proxy mode can offer better performance than the MPC mode, as it avoids the computational overhead of the multi-party computation protocol. However, it introduces a new network assumption: the attestor must ensure that it is indeed communicating with the intended server, mitigating any potential risks of miscommunication or attacks.
Primus’ Proxy mode differs from others in the industry by leveraging the highly efficient QuickSilver protocol during the proof process. Additionally, it proves the Key Derivation Functions (KDFs) during the TLS connection establishment, which is typically inefficient in zk-SNARK alternatives. This approach also eliminates the need for extra padding, which can be limiting and lack generality.
The diagram below illustrates the general workflow of how the Proxy mode operates.