What is Primus
What is Primus
Primus (formerly "PADO") is building the future of data interoperability. The mission of Primus is to enable secure, permissionless data verification and computation in blockchain and AI.
The Problems
As blockchain and decentralized technologies continue to evolve, they encounter critical challenges, including limited on-chain data, fragmentation between Web2 and Web3 systems, and the difficulty mature industries face in leveraging decentralized networks effectively. Traditional systems fail to deliver the privacy, scalability, and interoperability required to overcome these obstacles.
A key issue with AI in decentralized systems is the absence of transparency and accountability. Without verifiable mechanisms, users cannot trust AI’s actions, decisions, or data management, raising concerns about potential manipulation, security vulnerabilities, and privacy breaches.
Our Solutions
The challenges we face today point to one clear solution: a cryptographic layer. This layer securely connects off-chain data with blockchain and AI systems. Primus tackles this by leveraging verification and encrypted computation to introduce valuable data into these ecosystems, empowering data owners and enabling a world where data can flow freely, unlocking its full potential.
Primus also provides developers with easy-to-use APIs. Think of it as a bridge, linking foundational blockchain and AI ecosystems with the diverse applications being built on top.
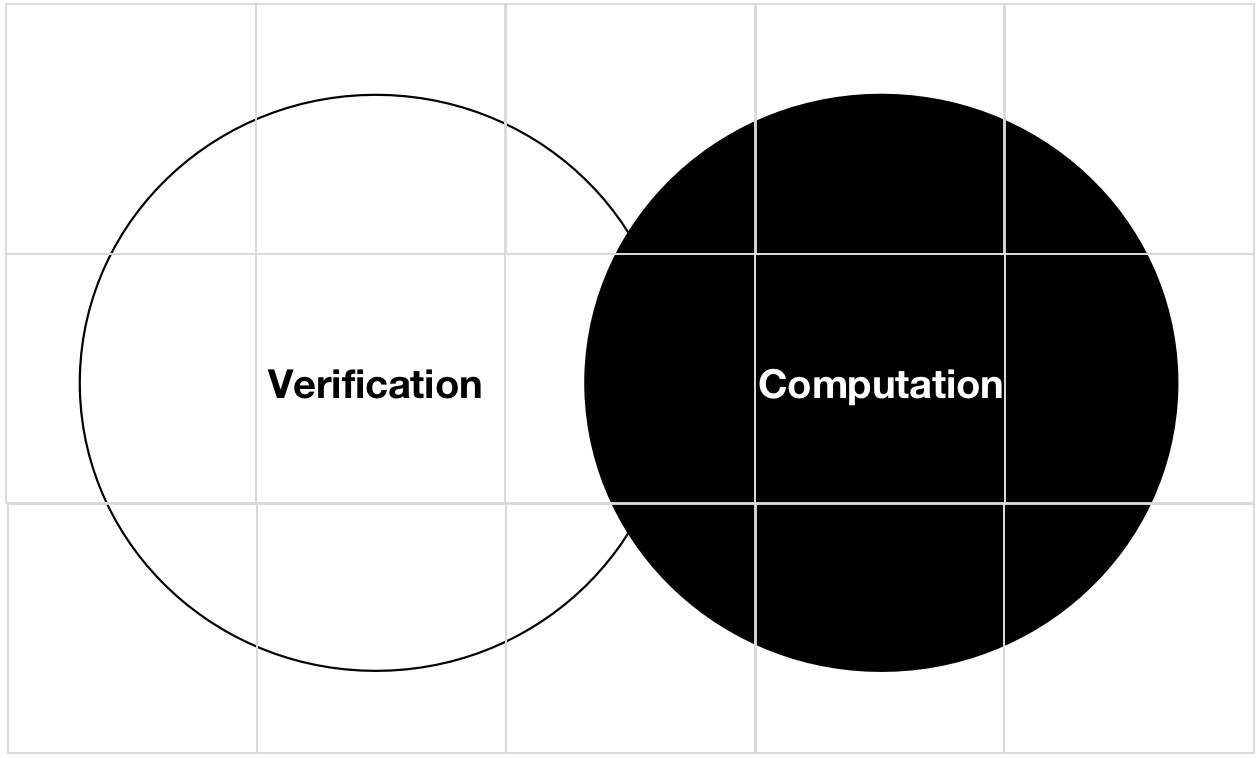
Core Technologies
Our technology focuses on two key innovations: zkTLS and zkFHE. zkTLS builds on the Transport Layer Security (TLS) protocol by adding zero-knowledge proofs, so you can verify data authenticity without revealing the data itself. zkFHE takes this a step further, ensuring computations on encrypted data are secure and tamper-proof, even when outsourced.
- zkTLS Resources:
- zkFHE Resources: