Data Computation Network

Data Computation Network
Overview
The potential value of data is increasingly recognized by enterprises and individuals. People's daily behavioral data provides corrections and feedback for different technology products, creating economic value and social impact. The effective mining of data value and the avoidance of individual privacy violations as much as possible are the main pain points in the process of data monetization.
Existing systems built from either zero-knowledge proofs, multi-party computations or other privacy-enhancing techniques cannot fully resolve the paradox of privacy protection and utilization of sensitive data, and various computational issues during data processing require further reliable integrity measures.
Leveraging the benefits of traceability and programmability from blockchain-like techniques, Primus' zkFHE protocol enables an open infrastructure for librating data value with verifiable and confidential data processes while individual and organization developers can selectively contribute with either security, functional scalability and effectivity to the network.
The core advantages of zkFHE lie in its natural abilities from both zero-knowledge proofs and fully homomorphic encryptions, to perform customizable computations on encrypted data, with the correctness guaranteed by validity proofs for the whole computation circuits. The validity proofs solids the whole computation framework with cryptographic and computational trustlessness to facilitate the necessary security requirements of applications.
Roles in Data Computation Network
Data Provider
A data provider is an individual or organization that provides computing data to Primus Network. The data from the data provider is encrypted by the FHE algorithm and then uploaded to decentralized storage blockchains such as Arweave and Filecoin. A data provider can receive a portion of the computation fee for the data usage.
Worker
A worker is a node of Primus data computation network, providing computing resources, running the zkFHE algorithm on encrypted data, and providing with a confidential computing environment and resources. A worker needs to generate a zero-knowledge proof while computing.
A worker also needs to provide the Data Encryption Public Key to a data provider to encrypt the data, and meanwhile, it needs to re-encrypt the confidential computation results into results that only the caller can decrypt.
zkFHE algorithm naturally guarantees data confidentiality and computation integrity. Workers can earn computation fees from the successful execution of a computation task.
Caller
A caller is an individual or organization that uses the computation capability and data resources of the network. The caller can specify the encrypted data uploaded by the data provider to initiate a computation task and obtain the result from the task execution. Caller shall pay for the computation service.
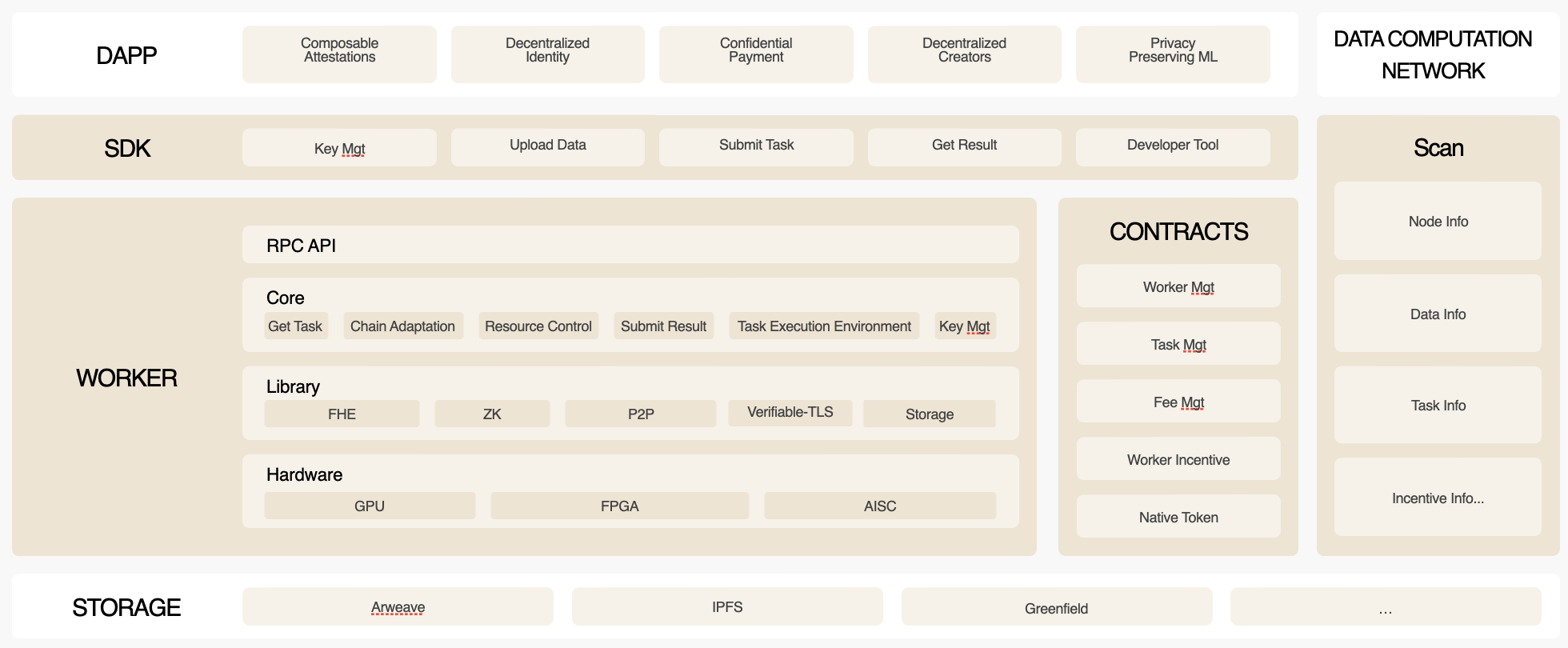
Network Architecture
With comprehensive consideration of decentralization, security and scalability, the network is designed to separate consensus and computation for scalability. Workers mainly use the zkFHE algorithm to run confidential computations and generate proofs for integrity assurance. The proofs are verified through Primus contracts. Meanwhile, multiple modules including worker management, data management, task management, fee management, and worker incentives, compose Primus contracts.
Components of Primus Data Computation Network
Worker
As mentioned here, workers are the key components that support confidential computation tasks to maintain the network liveness.
Primus Contracts
Primus Contracts are a collection of blockchain-like smart contracts deployed in multiple blockchains, including Ethereum, L2s, AO, and others. Primus Contracts consist of multiple modules including worker management, data management, task management, fee management, worker incentives, etc.
Primus Network SDK
Primus Network SDK is a collection of developer tools. Developers can leverage the data computation capability of Primus Network through this SDK and implement various privacy-centric applications that can be alive in the Network.
Primus Scan
Primus Scan is a user interface for exploring the information of Primus data computation network. Through Primus Scan, one can find the details about workers, computable data, tasks, etc.
Logical Architecture
The following figures show the logical architecture within the network.
Workflow
According to the classification of data encryption keys, the patterns of FHE algorithms execution within Primus data computation network, can be divided into the following three categories. One may find more explanation about the three types of application modes that adapt to different types of callers.
- Threshold FHE: Use the shared public generated by multiple Workers to encrypt data. Note this is a technical representative of joint-worker mode.
- Single-Key FHE: Use the user's own key to encrypt data. Note this is a technical representative of single-user mode.
- Multi-Key FHE: Use the public keys of multiple Workers to encrypt data. Note this is a technical representative of selective multi-worker mode. We emphasis the name of "Multi-Key FHE" here is differ from the Multi-Key FHE algorithm in academia.
Core workflow can be divided into three categories accordingly.
1. Threshold FHE Core Workflow
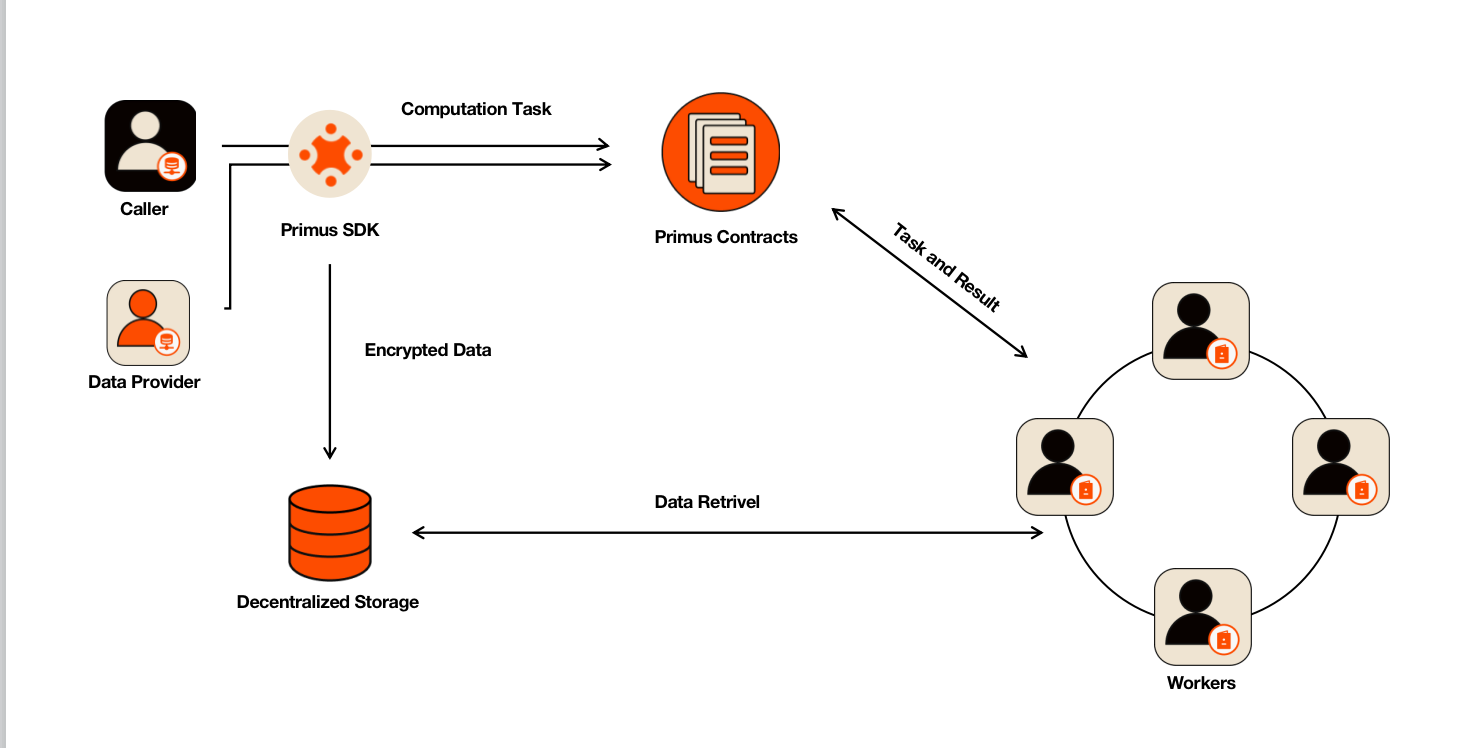
Worker Registration
An eligible worker must be registered with the worker management module of Primus contracts. Confidential computation tasks shall only be dispatched to successfully registered workers. The registered information includes name, description, owner address, machine resources, RPC address and port, worker's public key, etc.
Task Submission and Data Encryption Public Key Generation
A caller can submit a confidential computing task through an application developed based on Primus Network SDK. To launch a confidential computation task, it is essential to pay the required fees for the computation and data resources. When a caller initiates a task, he shall publish his own public key, for which the final encrypted computation result is only derivable with regard to the private key paired to that public key.
Then the Primus Network SDK forwards the submit_task request to the task management module. The task management module selects a group of workers who generate the data encryption public keys, and another group of workers who execute the task. In practice, the two worker groups can be the same. The first group of workers returns the data encryption public keys to the task management contract.
Data Upload
A data provider uses Primus Network SDK to obtain the data encryption public keys required by the task from the task management module. The data provider uses the FHE algorithm with those data encryption public keys to encrypt the data and upload the ciphertexts to a storage blockchain such as Arweave.
zkFHE Computation
The Workers who are designated to execute the task shall get the task information from the task management module, and also retrieve the encrypted data from the storage blockchain. They execute the zkFHE computation and output both the encrypted result and a validity proof.
Re-encryption of Result
The Workers who generate the data encryption public keys shall re-encrypt the encrypted result after the task execution, using the caller's public key, so that only the caller can decrypt the result correctly.
Proof Verification and Fee Settlement
After the task execution, workers upload the encrypted result with the validity proof to the task management module. After the task management module successfully verifies the proof, it will invoke the fee management module for fee settlement. The fee will be distributed to the data providers and workers according to the requirements specified in the task.
Decryption of Result
The caller uses its own private key through the FHE algorithm of Primus Network SDK for decryption, and obtains the raw result.
2. Single-Key FHE Core Workflow
Single-Key FHE core workflow is similar to the Threshold FHE core workflow, with the following main differences:
- The Caller and Data Provider are the same person.
- When selecting Workers, you only need to select the Workers that execute the task, not the Workers that generate the data encryption key. This is because the Single-Key FHE uses the user's own key to encrypt data.
- The Result Re-encryption process is not required because the data is encrypted using its own key.
3. Multi-Key FHE Core Workflow
Register Worker
The Multi-Key FHE register worker process is the same as Threshold FHE Register Worker.
Get Workers Public Keys and Upload Data
Data Provider submits data upload request to Task Management of Primus contracts. The Task Management selects which Workers' public keys will be used to encrypt the data, and these workers will be responsible for executing tasks based on this data.
And Data Provider uses Primus Network SDK to obtain the Workers' public keys required by the data upload request from Task Management of Primus contacts.
Then Data Provider use the FHE algorithm of Primus Network SDK and the Workers' public keys to encrypt the data and upload it to Storage Blockchain such as Arweave and Filecoin.
Submit Task
Caller can submit a confidential computing task through an application developed based on Primus Network SDK. Initiating a confidential computing task requires paying a certain amount of computing and data fees. When Caller initiates a task, it will pass its own Caller Public Key, and the final encrypted computation result is only the private key corresponding to the Caller Public Key can be decrypted.
zkFHE Computing
The Multi-Key zkFHE Computing process is the same as Threshold zkFHE Computing, but run different zkFHE algorithms.
Proof Verify and Fee Settlement
The Multi-Key FHE Proof Verify and Fee Settlement process is the same as Threshold FHE Proof Verify and Fee Settlement.
Decrypt Result
The Multi-Key FHE Decrypt Result process is the same as Threshold FHE Decrypt Result.